Adjusting Azure tagging policies
Posted
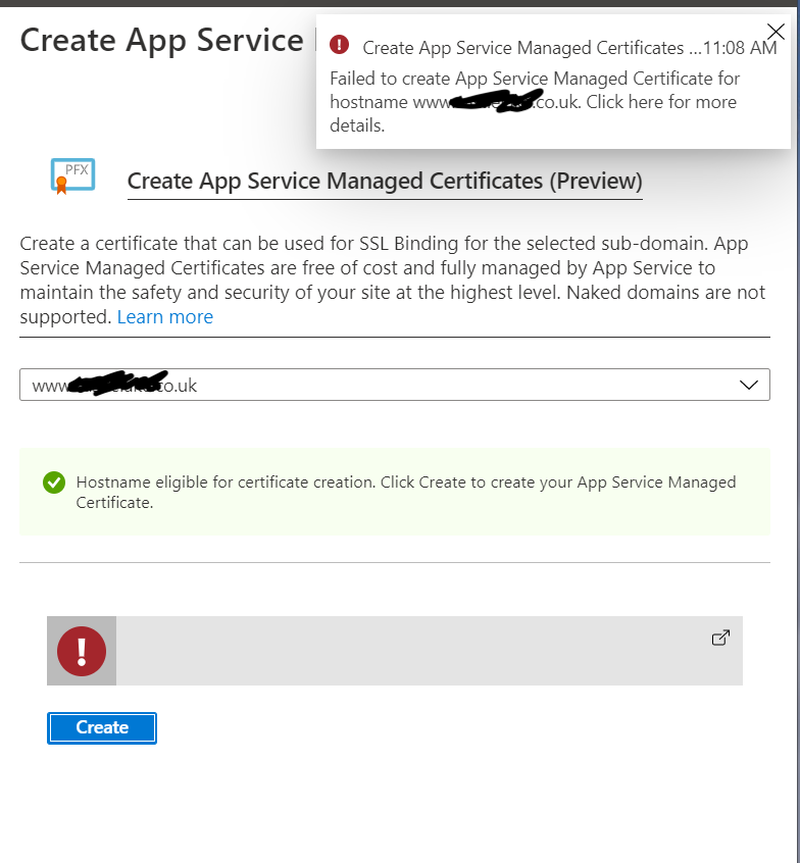
App Service Managed Certificates are one of the many wonders of the Azure world. No messing around with Lets Encrypt, just prove to Azure that you own the domain (via a TXT record) and free, rotating, certificates can be yours with a couple of clicks.
We use them for HTTPS on our 301 Redirect function I wrote about previously. Adding a domain this week I received the above error. Of course the “click for more details” didn’t work so, for a day or two, I was in the dark.
Then a colleague reached out and said they were having trouble creating alerts: the lightbulb went off. We recently added the Require a tag on resources policy to our subscription to ensure that all new resources are tagged by utilization - thereby permitting better cost allocation across business units.
The issue, with alerts and certs, is that neither of these resource types support tagging. Betting that the anonymous error was a result of the policy, I temporarily disabled it and was able to create the certificate, avoiding a support call to Microsoft.
But how to get the policy to work correctly? The solution was to clone the built in policy and add exceptions for resources we’re using that don’t support tagging. Here’s the policy in full:
|
|
I’ve highlighted the key lines, starting at 24. Essentially the policy does an and of
- an exists check on the tag combined with
- checking the type field is not one of the provided values.
A quick way to find applicable resource types is to look for any resources failing the policy check and copy/paste their type in.
Pretty easy once you figure it out. I hope you find it useful.